EPM Common Uses and Steps
EPM runs as an agent-based Windows service that can monitor an endpoint by recording activity logs, software permissions, processes, offline access, and agent status.
Allow Normal Users to Elevate Application On-Demand
Scenario
Business needs might demand users to access new applications on their systems. For example, a developer (with standard user rights) might be required to access a remote meeting application. Without administrator privileges and underlying policies, the user will not be able to access this application. The user can create requests for adding the new application to a trusted applications list or one-time permission to install/use the application depending on circumstances or organisational requirements. There are provisions to configure automatic approvals whenever required. In such cases, the users will get instant approvals for their requests.
After installing the EPM agent you can use it to Elevate an application depending on the policy associated with your account. See the following steps in order to elevate an application on-demand:
Right-click on the application you need to use to view the drop-down menu and select Elevate with Sectona EPM.
There are three scenarios wherein:
The assigned user policy lets you access the application.
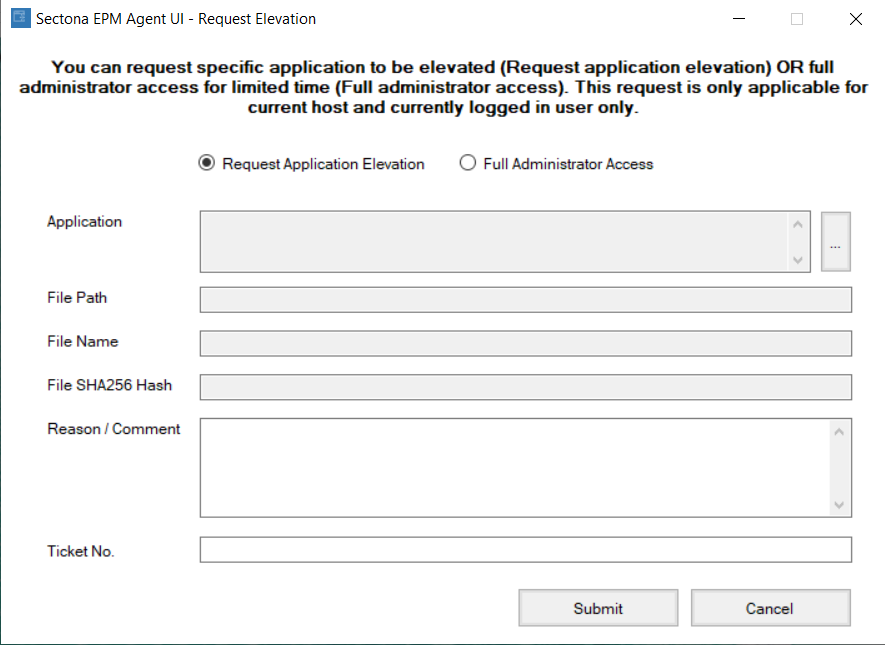
The assigned user policy denies your access. In case of access denial, you will have to request access by right-clicking on the agent icon from the System Tray located in the taskbar and select New Request. Then you will see this window pop up:-
Browse the application you require access to and the details will be filled in automatically.
Enter the reason for access and Ticket No.
Enable Users with Controlled & Temporary Administrator Access
Scenario
Quite often, certain users might have to carry out multiple tasks that require broader administrative privileges. Granting uncontrolled, unmonitored full administrator access will defeat the principle of Least Privileges. The system offers a robust way to handle such a critical requirement. Users can raise a request for administrator rights for a short time. They will have to provide a reason to justify access needs. The system administrators will review the request and grant time-limited administrator privileges to the user and continuously monitor the admin rights on a periodic basis. The standard user will be able to perform all tasks that require administrator privileges, but everything will happen under full controls and audits. At the end of the approved usage period,
The temporary administrator privilege will be automatically revoked.
All processes and applications elevated during that period will be terminated.
All activities done by the user are captured as audit trails.
There are options to request approval well in advance to carry out planned tasks.
Users can request for administrator right access for a specific application or time limited access to perform administrative tasks.
Right-click on the application you need to use to view the drop-down menu and select Elevate with Sectona EPM.
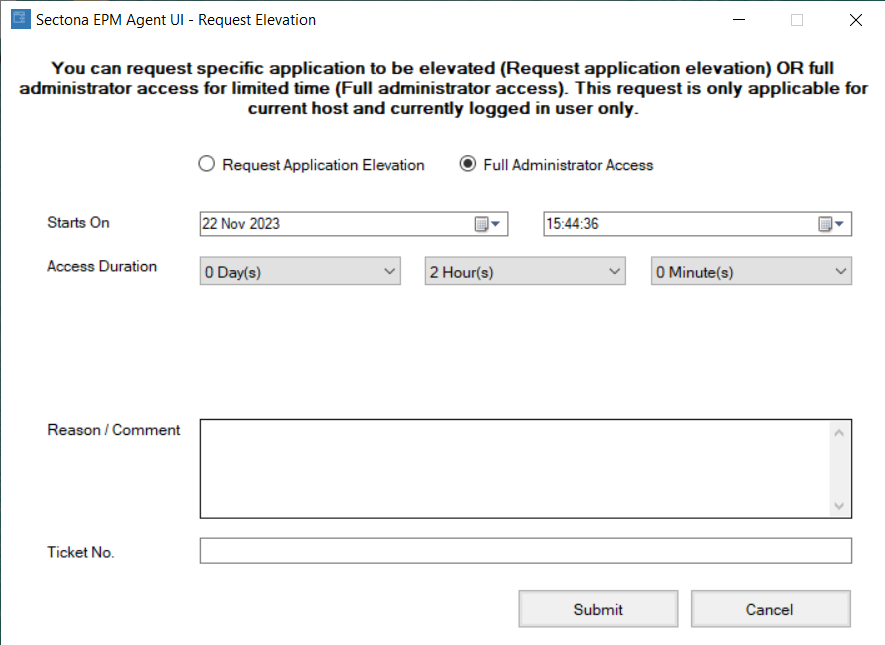
From the window pop-up select the Full Administrator Access option.
Enter details for the duration for which you require administrator privileges.
Enter the reason for access and Ticket No.
Application Control
Scenario
Losing access to complete tasks:- Consider a user in your department would usually run a list of applications and processes to complete their tasks. Now if these applications that require unrestricted access by this user to do their job have now been blocked due to some updates or changes in privilege management. The same applications now requiring local admin rights to install, run, and update them. When the local administrator rights are removed and the user is made a standard user, the applications cannot setup or load the latest versions.
EPM :- The system with Endpoint Privilege Management enables the user (with just standard user rights) to run all applications without any interruptions and without the need to know the password of the administrative user. The system administrator can create a policy marking the list of applications as trusted and permit the user to run those applications on a specific computer or multiple computers.
EPM Agent:- The EPM agent installed on the end user’s machine elevates the applications for that standard user. The elevation of privileges is based on the control policies in place. If a policy does not exist for the application, the user can place a privilege elevation request and access the application on approval. While local administrator rights stand removed, user experience is not compromised, and productivity is not impacted.
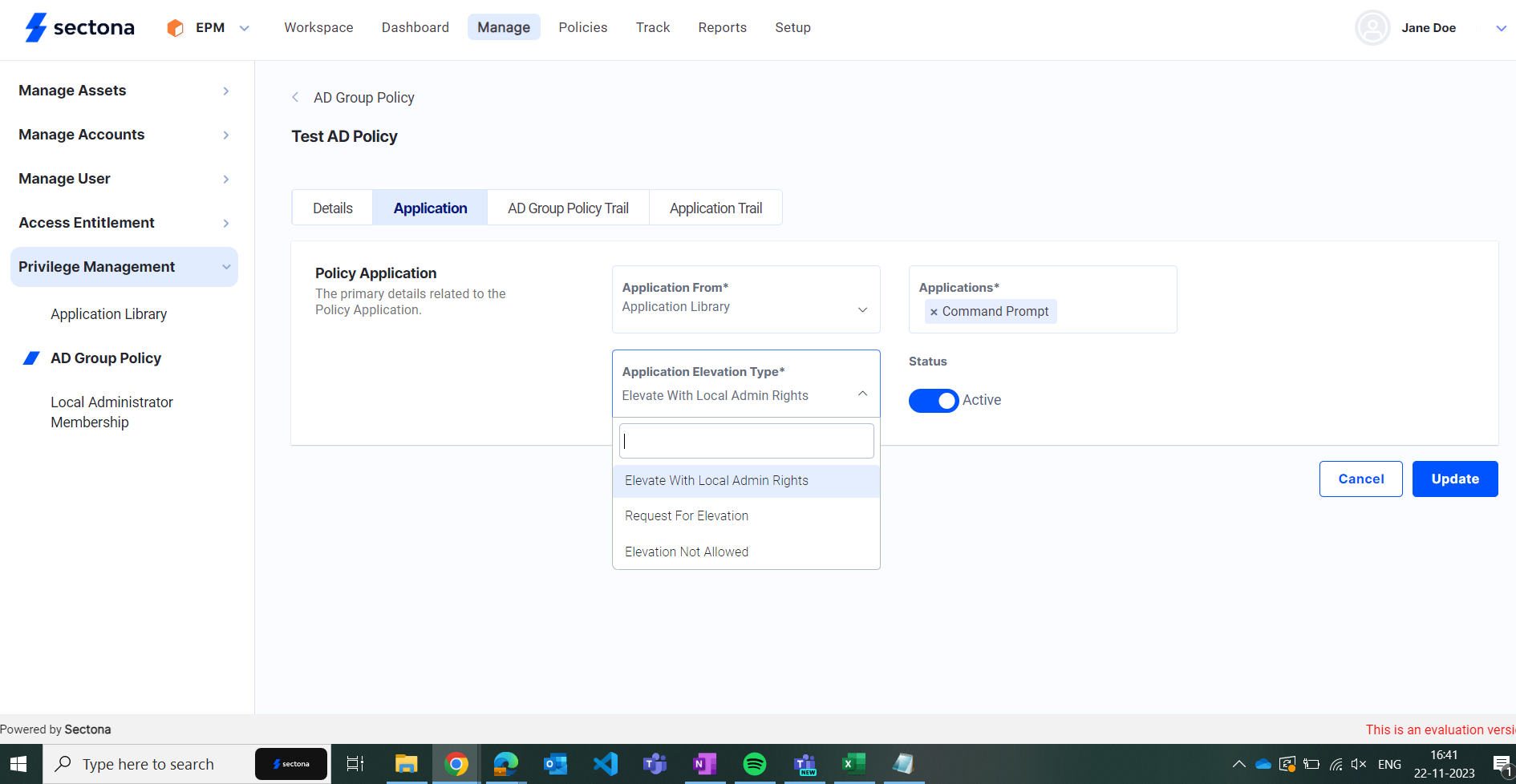
System users can grant or block access to specific applications or any type of malware respectively by creating an AD Group Policy. Consider the following steps:
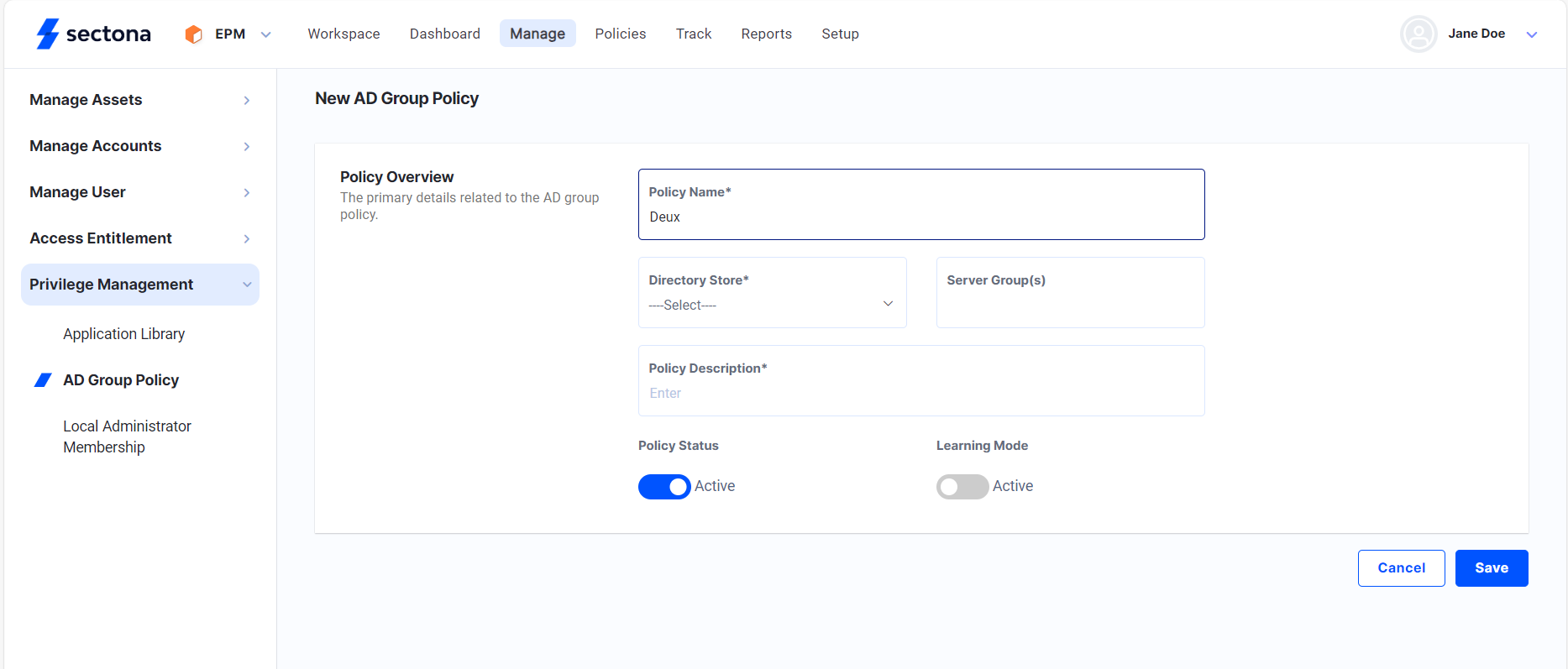
Select EPM from the Product Navigator.
Click on Manage → Click on Privilege Management from the sidebar → select AD Group Policy.
Enter policy name and select the Directory Store.
This will automatically fill the Server Group(s) within that Directory Store.
Enter Policy Description, the status of the policy is set to Active by default.
Select the policy designated application you would like to edit and click on the pen icon.
Elevate With Local Admin Rights lets you use applications with administrator privileges.
Request for Elevation is used in case of admin rights elevation is not accessible.
Elevation Not Allowed is when an application has been blacklisted from the endpoint.
Offline Scenario
Scenario
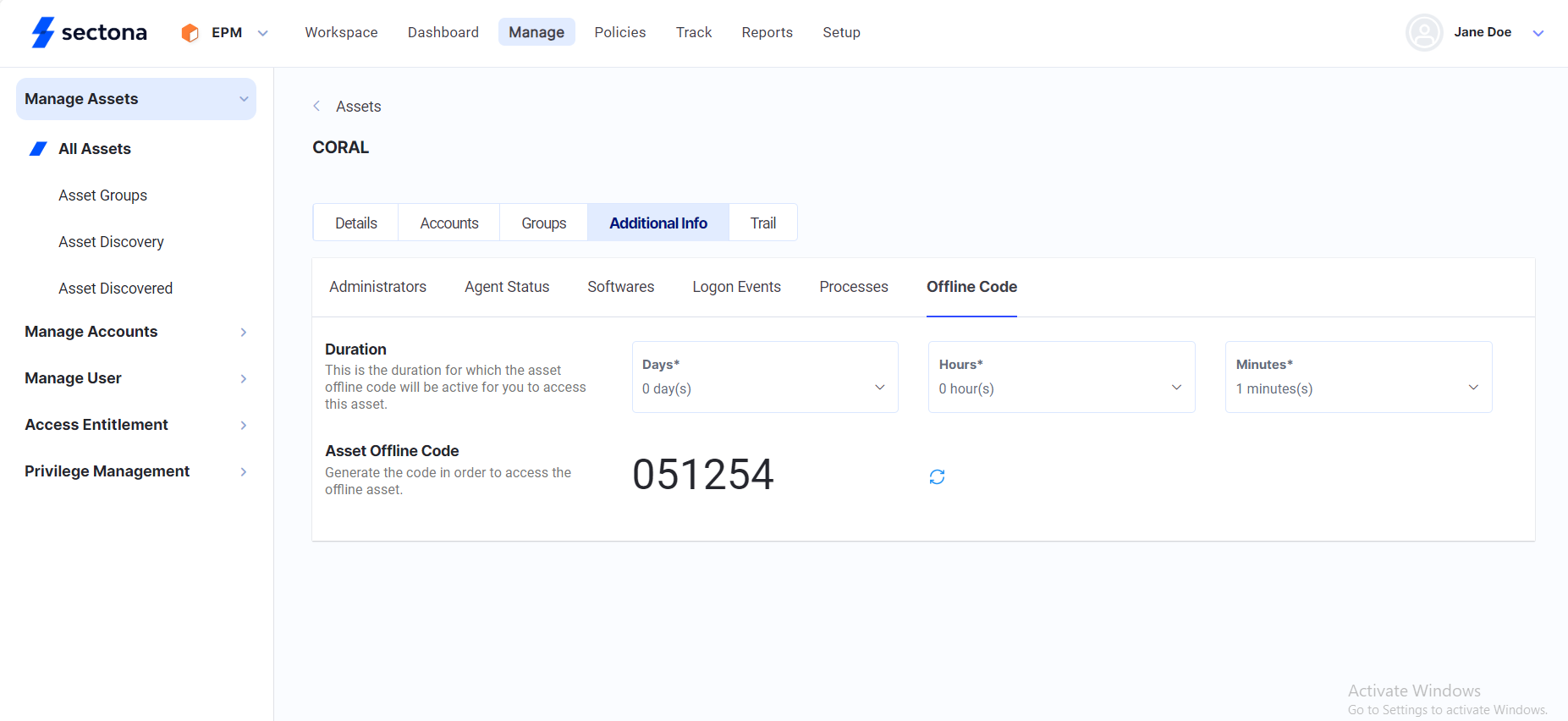
A user might be working from home or be disconnected from the office LAN. If a local system administrator rights are removed without taking care of these scenarios, it will lead to frustrated end users and result in productivity loss. The system handles these scenarios in such a way that the least privileges are enforced, same as the online scenarios. The policies created by the administrators are cached by the EPM agent. In offline scenarios, the agent takes care of enforcing the recently cached policy. Users will not face any difficulty in running the required applications. In this case the user just needs to request for a offline code from the system admin and apply it in the appropriate section to get the things done accordingly
In scenarios where the EPM server is unreachable due to network unavailability, Sectona provides an Offline Code feature for the on-time access. The Offline Code is generated on the EPM server and when needed can be acquired from the EPM Administrator.
Right-click on the application that you want to elevate.
Click on the “Elevate with Sectona” option.
You will see an offline-verification pop-up on the screen.
Enter the offline code provided by the Administrator.
Click on the OK button.
You will get the access to the elevated application.
Remove & Continuously Monitor Administrator Rights
Scenario
Issue no 1: - When users possess local administrator privileges, they tend to install unapproved software for personal use. Such software could be malicious and open the doors for hackers. The endpoint may be compromised, and attackers can move laterally across the network.
Issue no 2: - When users possess local administrator privileges, they can create a backdoor user which they can use to accomplish their malicious intent. Sectona EPM removes local administrator rights from endpoints, thus preventing users from installing or using unapproved software and remove the backdoor user. While removing local administrator rights prevents the use of unapproved software, the system ensures that the user experience and productivity are not affected. Administrators can define policies that enable standard users to run the applications needed for work without any interruptions.
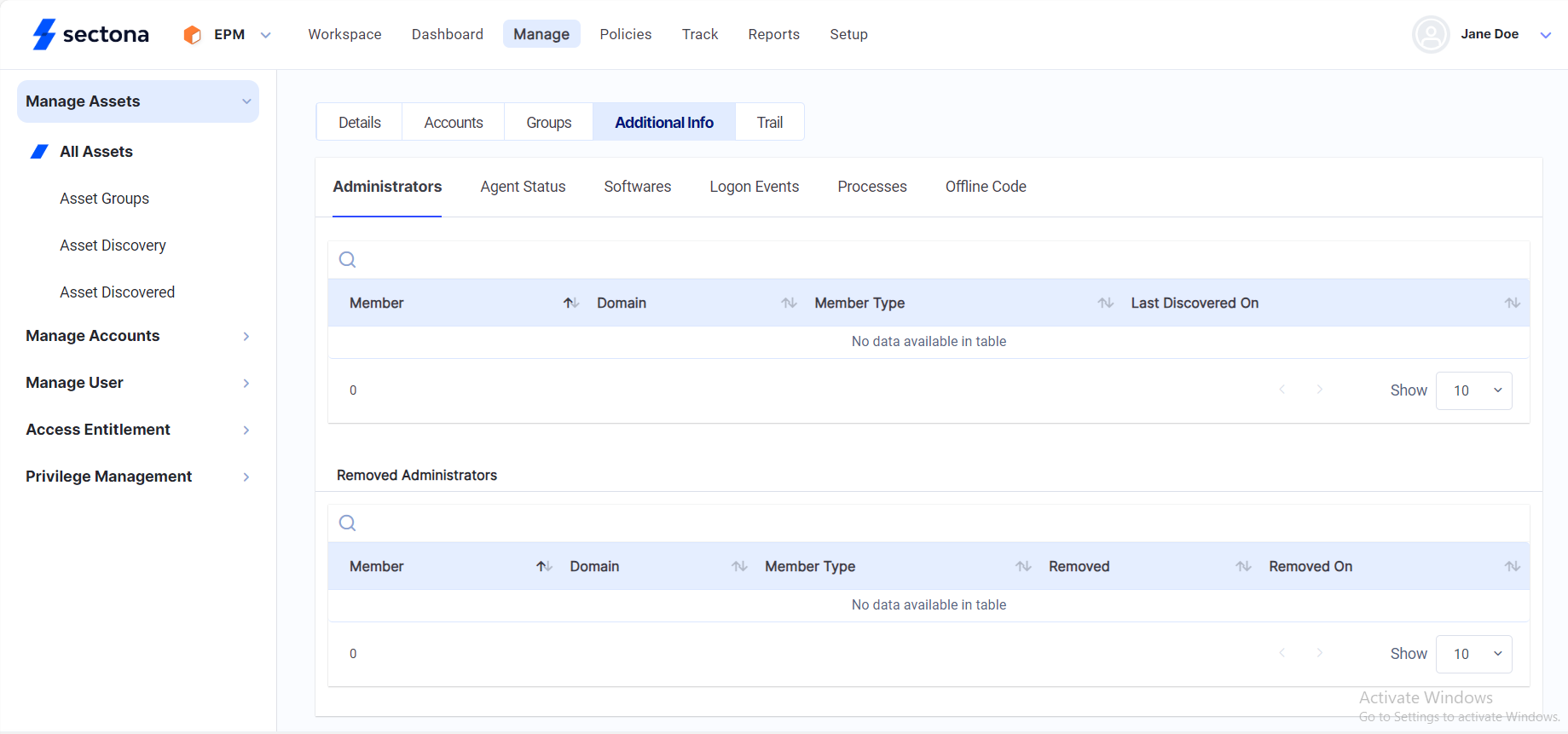
You can monitor administrator right of a particular user from the following steps:
Select EPM from the product navigator
Select Manage from the navigation bar → Manage Assets → All Assets.
Click on more options of the Asset you would like to monitor → click on Additional Info.
Here you will be able to view the details regarding Administrators, Agent Status, Software, Logon Events, Processors and Offline Code.