Architecture, flow, & advantages of PTM
The basic idea of Privileged Task Management is based on how the system works with respect to its functional behavior. This functional behavior is shown under the architecture of Privileged Task Management below. It describes functional and backend process of how the can task is created, assigned, executed and deleted. Apart from the backend process, there are flowcharts given below which shows the frontend process of how task can be created, assigned, executed and deleted.
This section covers:
The architecture of PTM
The task is a sequence of commands that can be executed only with help of privileged access. Executing a task on Sectona PAM requires the user to login to PAM. Consider a task is built under PAM for the logged-in user. Once the user initiates the task execution by clicking on the run icon, PAM retrieves the password of the privileged account, selects the communication protocol accordingly, logs in into the target server, and executes the task. Once this task is executed, the output of the task is stored/logged into PAM and the output is then shown to the user.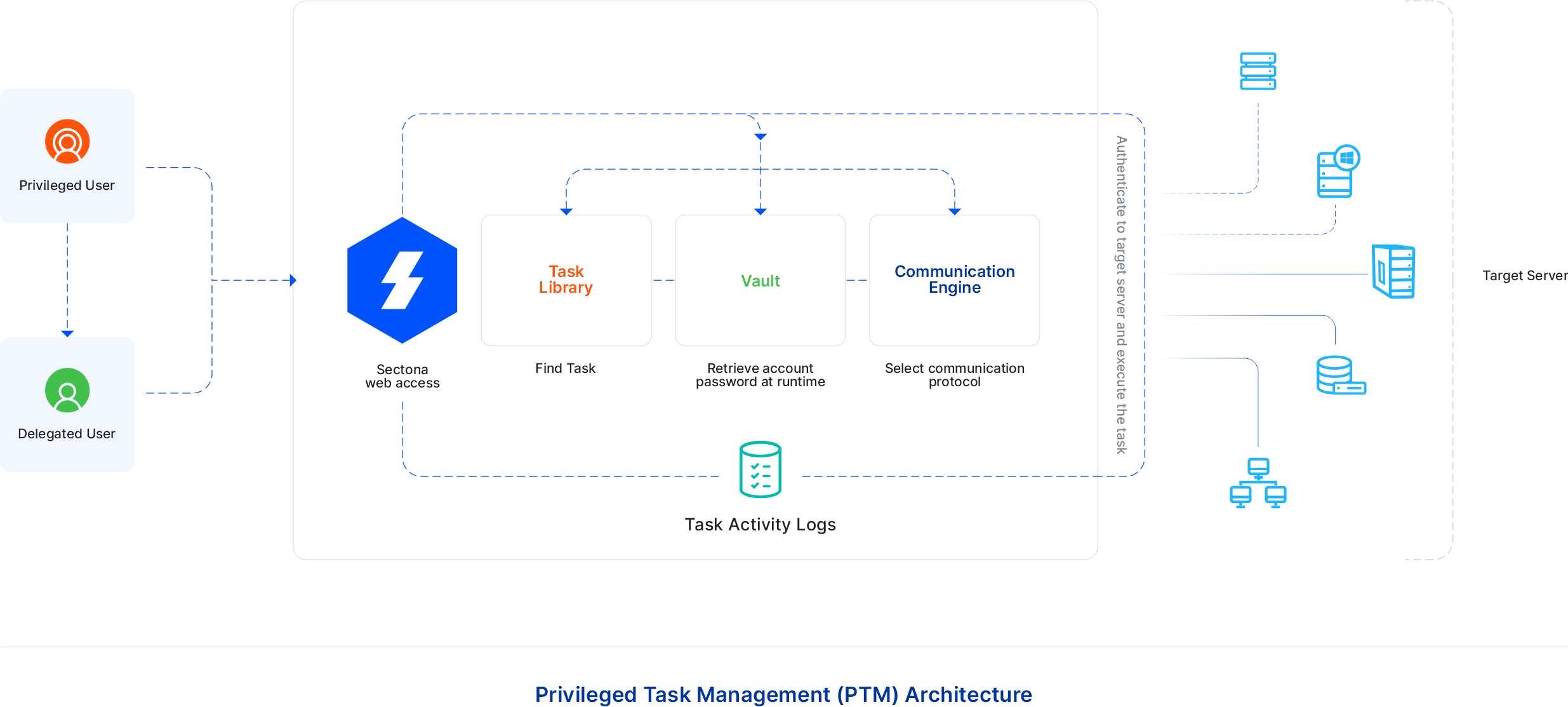
Flow of PTM operations
The flow of importing a new task library
PAM User authenticates Sectona. To add a new task, go to Manage > Task Library > Here you’ll find all the list of predefined tasks as well. Click on +Add Task Library Add Name, select its base access type according to the command you wish to execute. Enter the command. Enter the input field name if necessary. Choose the pattern of the log display and save it. After adding a new task library in PAM, the user can execute this library as and when needed by configuring a task with appropriate asset and account: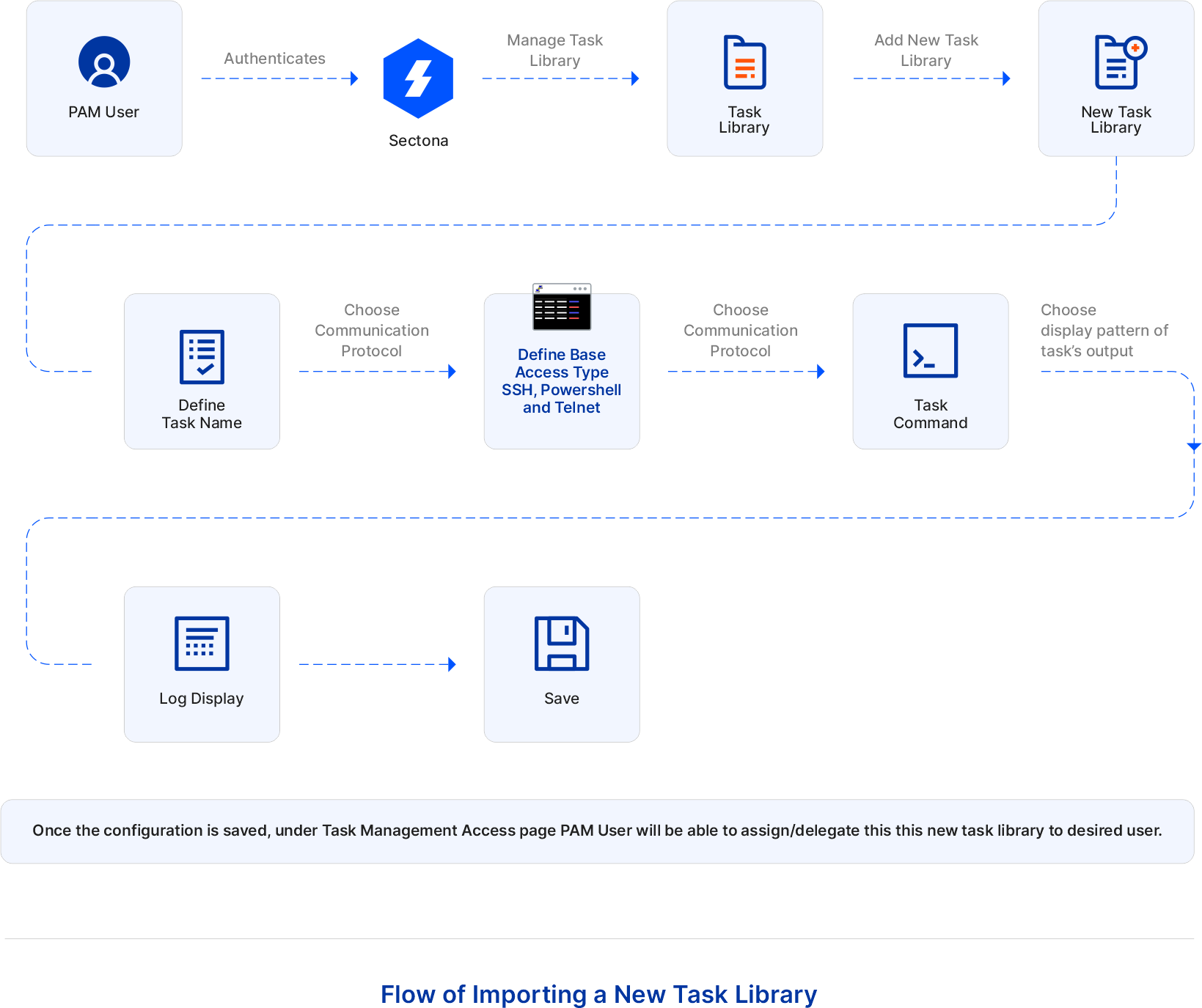
The flow of user executing a privileged task
PAM User authenticates Sectona. Users can execute the privileged task without knowing the password of the privileged account. Go to Access - Task Management. Private/Delegated tasks will be shown here. Select and run one of the tasks say, ifconfig command, and wait for its execution to get completed. Once the execution is completed and its current status is shown as Not Executing, check its history to view the action status and output of the task: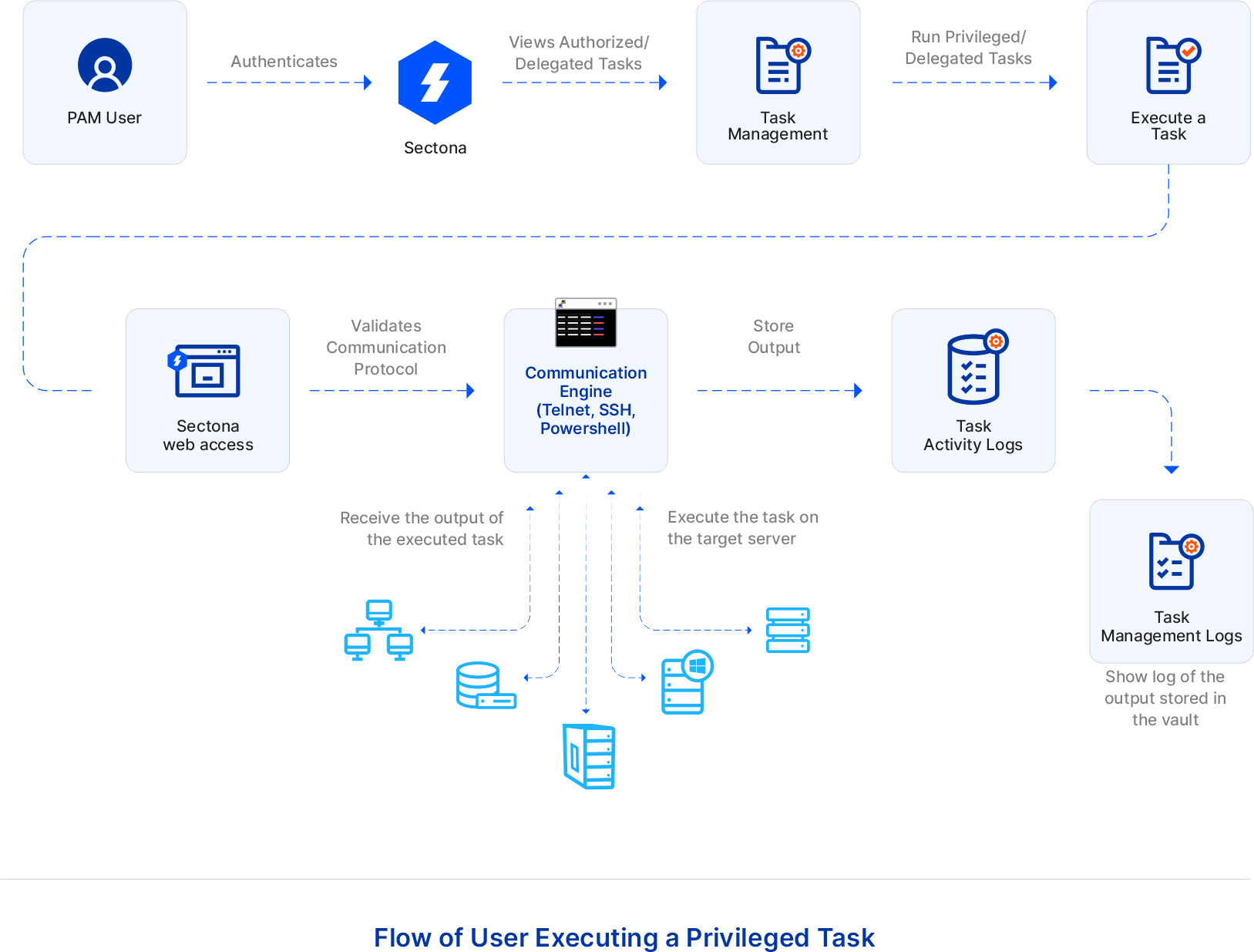
The flow of user delegating a privileged task
PAM User authenticates Sectona. Users can execute the privileged task without knowing the password of the privileged account. Go to Access - Task Management. Private/Delegated tasks will be shown here. Click on +New to configure a task. According to the base access type (SSH, Telnet, or PowerShell) of the task, select the privileged account. Now select the user you wish to delegate this task to and save the configuration. Once the configuration is saved, the delegated user when logs into Sectona PAM, the task delegated to the user is shown under the Task Management Access page: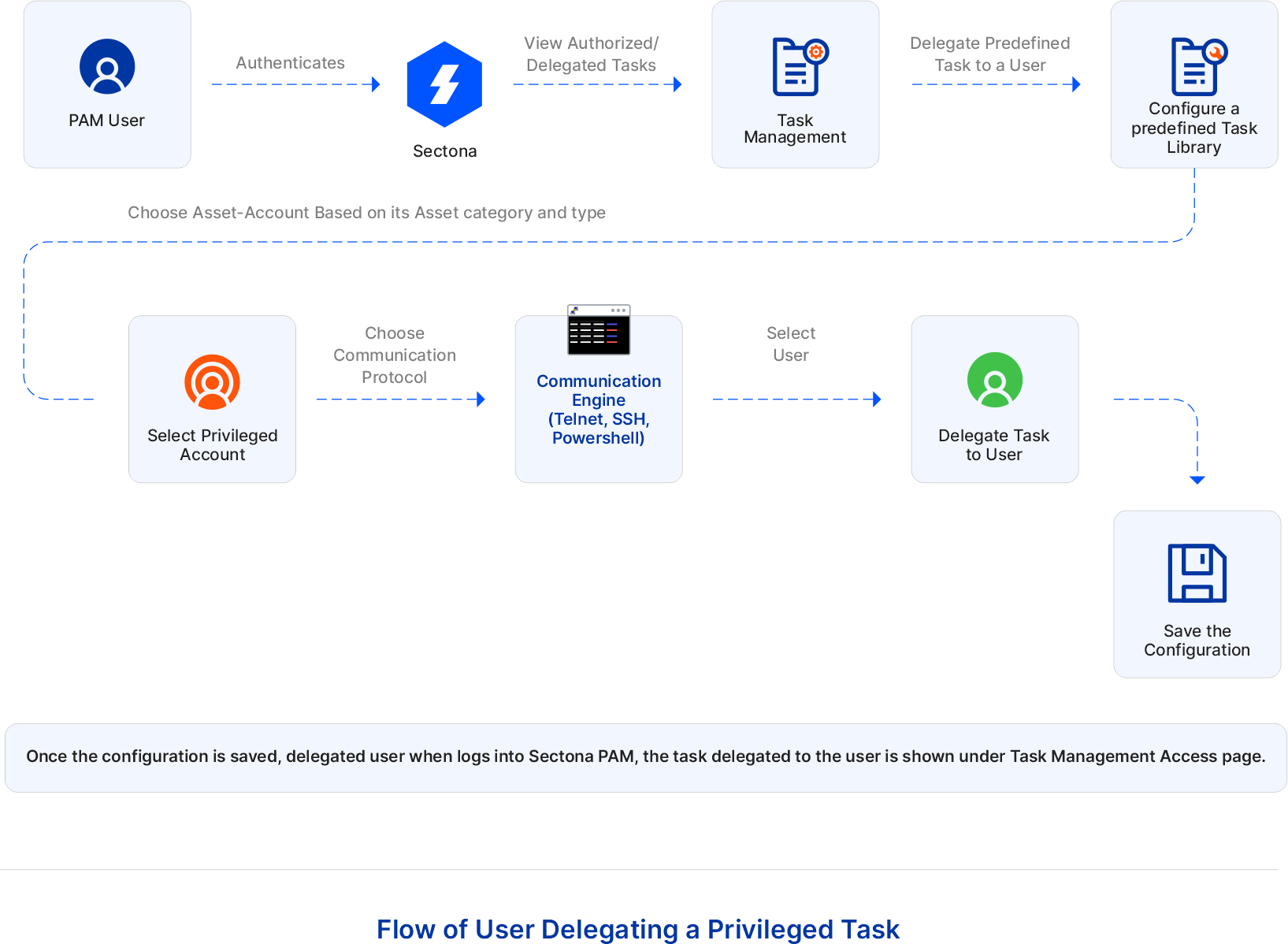
The flow of user creating a task bucket
PAM User authenticates Sectona. User can create a task bucket where he/she can add one or more than one task and privatize/ delegate task to one or more than user by following few steps. Go to Access – Task – Task Bucket. Configure task bucket by clicking on +New. If delegating, select one or more than one user according to the need. You need not select any user if privatizing. Once users are select, enter the task bucket name. Now choose a preconfigured task by selecting one or more than one configured task according to the need and save the configuration. Once the configuration is saved you can execute the task bucket by clicking on its run button. Users can also run one or more than one task bucket by selecting the task buckets and clicking on Execute Selected: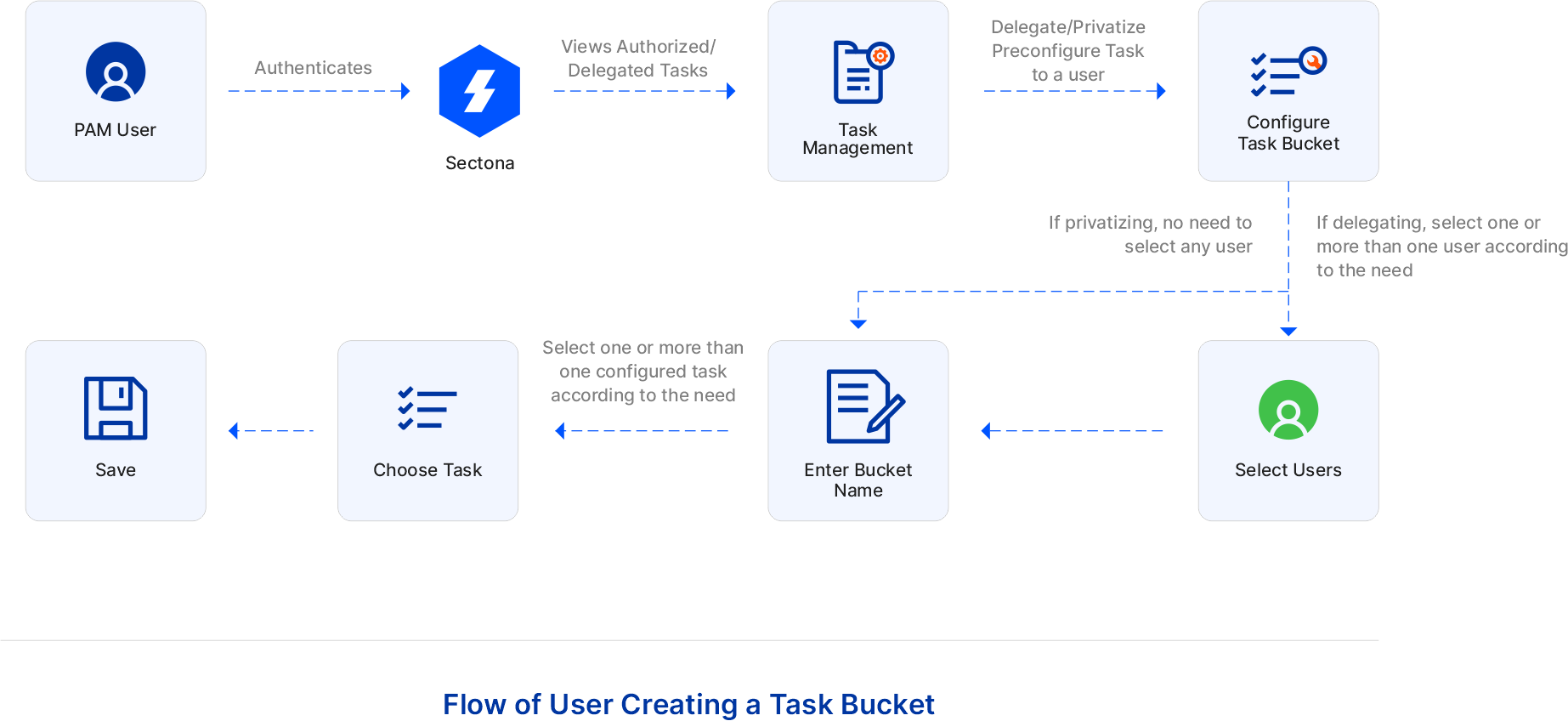
Advantages of PTM
- Privileged Task Management helps in executing the tasks that address issues that are commonly encountered on systems, applications, or devices that have well-known resolutions.
- Frequent support calls can also reduce common issues encountered on the system and can be solved easily without intimating any higher authority.
- This functionality enables users to control the actions of privileged users by placing limitations on what a user is allowed to do with an organization’s most critical asset.
- Design Your Own Task (DYOT) i.e. it enables the operator to create their task based on their specific requirement.
- Delegating the task to another person can lower the burden of the organization.
- Reduces system administrator’s backlogs and helps in automating IT processes.
- Complete access to the most critical asset is eliminated and restricted policy is maintained.
- Device-specific-knowledge will no more be required to the operator for executing any task.
- Dependency among people will be removed.
- Once a Task is created, it can be executed repetitively with just one click.
- Human error is eliminated as the process of executing a task is automated.
- The same task can be performed on different critical assets easily.
- Automating task activities can achieve notable resource-saving.
- Will help IT team to create task rather than executing it whenever needed.
- Organizations will grow faster concerning their IT unit.
