Getting Started
Every company provides user access to manage and support IT services and applications. It is common that users hold more access than they require. Misuse or abuse of access makes could lead to loss of data or mishandling of sensitive information. Managing and reviewing them from time to time becomes a vital task as mandated by several internal IT controls or by governance requirements. Manual reviews may lead to human error and make the task even more tedious.
Sectona's Privileged Access Governance (PAG) provides a fully consolidated, automated view of privileged users' access and entitlements. It provides an integrated view of three distinct data points such as users who can access infrastructure, user's entitlement to privileged accounts, and privileged accounts active in the enterprise IT.
The primary purpose of PAG is to analyze the entitlements, review user access, and track remediation actions. Solution makes it easy to examine and highlight risk of ungoverned access and excessive rights. It also allows action managers to take appropriate actions against remediation action. Solution enables certification and attestation of entitlement using automated workflows using flexible and easy to configure schedules.
How PAM & PAG works together
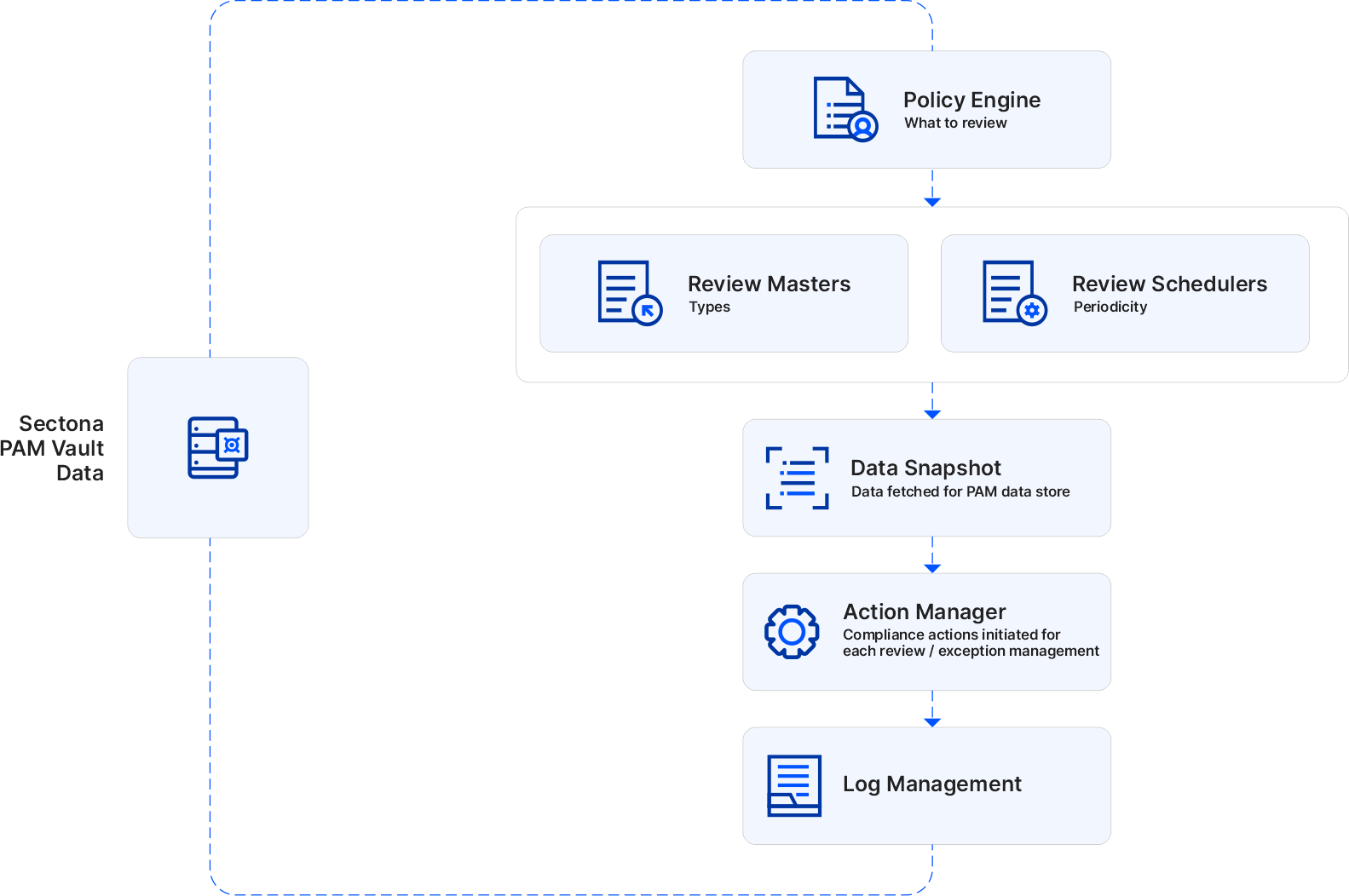
Privileged Access Governance is a policy-based approach to Privileged Access Management. Its functional behavior is shown under the architecture of Privileged Account Governance below. The documentary explains various elements in the architecture from the Policy Engine (Aggregate Data and review on a Periodical Schedule/Attribute-Based), the Review Masters (Approvers and Operations Manager approving/rejecting a request and take necessary action), and Log the activities (to process information in easy-to-digest reports and dashboards). Apart from the backend process, there are flowcharts given below. It shows the frontend process of monitoring privileged/non-privileged access and certifying by reviewing their sensitive information, assets, and applications situated across the organization's IT environment.
Privileged Account Governance allows administrators to raise a request for reviewing access details of users and accounts. This request is sent to PAG’s administrator, who is responsible for reviewing the requests. PAG Administrator submits the review by approving or rejecting the requests. If any request is rejected by the approver, the request is sent to the concerned operational manager pending action completion. Once the operational manager completes its review, its actions are recorded in the review. This helps the requester to know which rights can be given to which user and account.
Activating the PAG Component in Sectona Security Platform
PAG component can be activated for customer who are already using Sectona Privileged Access Management (PAM) component. PAG can be activated by adding required licenses to your PAM component. No separate installation of files or database is required. Find more information about adding licenses in Managing Licenses.
Please contact us with any issues, questions or comments at: support@sectona.com.
