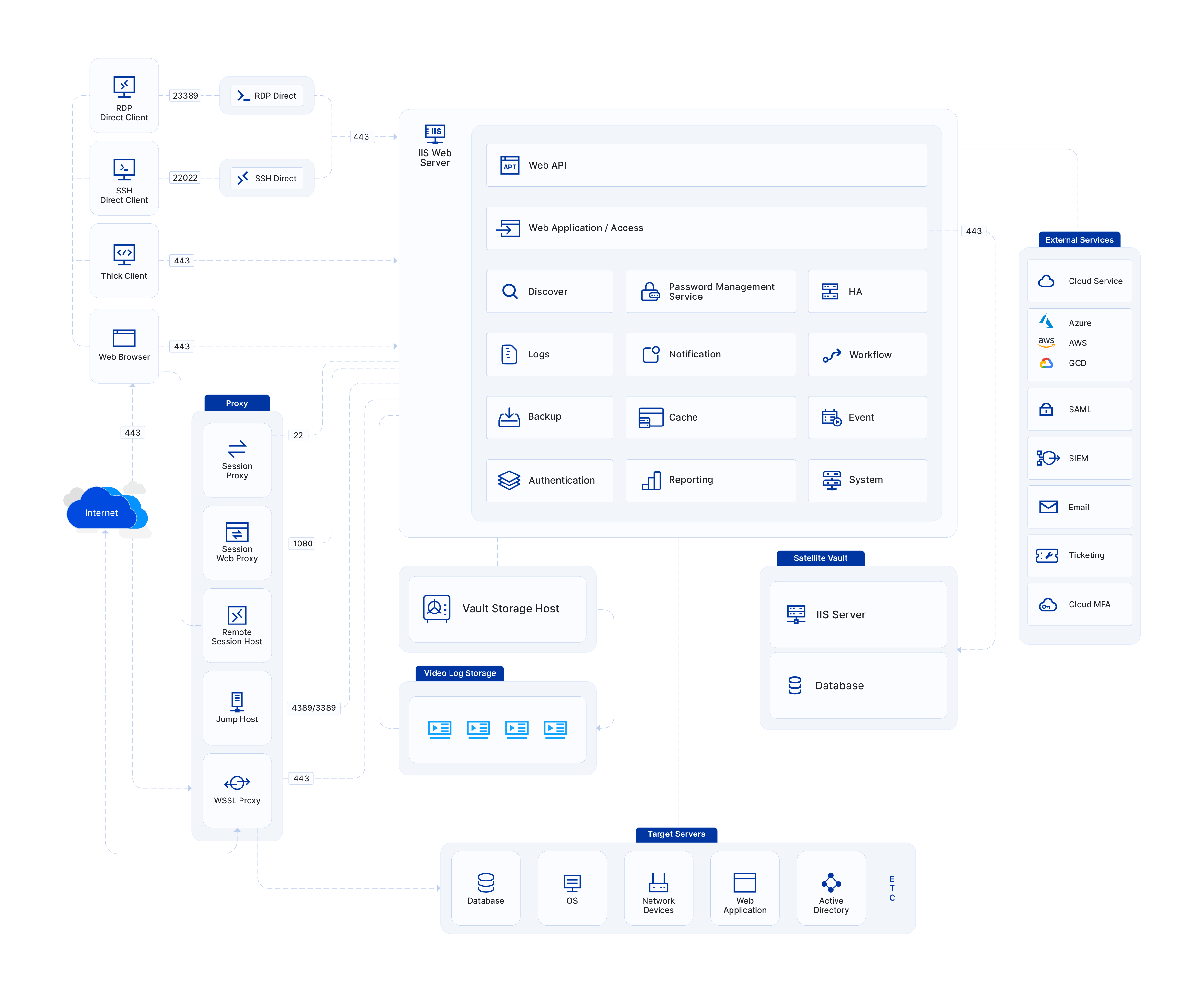
The Sectona system is built on service-based architecture leveraging Internet Information Services (IIS) as a web server and supporting MySQL embedded DB or Microsoft SQL as a vault options.
Enterprise edition is equivalent to MySQL embedded DB vaulting and Enterprise Plus allows external RDBMS vault deployments. All services or modules can be activated based on your licenses and additional modules must be configured as per requirement.
As the system is designed to leverage an IIS server all the application-related functional services can be managed through a central web portal of the system. This gives you the flexibility to manage application-related services remotely. For more information on managing services, you may refer to documentation in the section Monitoring System Health & Service Status
Component Characteristics
Sectona platform is a self-contained system based on .NET framework and related technologies. Sectona PAM platform uses the IIS web server and supports both embedded and external RDBMS to store passwords and configuration data. Multiple components of the system include:
Build Components
|
Component Name |
Description |
Built-In Web Access |
Support for Distributed Setup |
|---|---|---|---|
|
Sectona Web Access |
Web-based interface for the users and administrator to communicate with the vault and leverage system services. |
- |
- |
|
Vault Storage Host |
Secure, encrypted, tamper-proof storage for passwords, certificates, and keys. |
- |
Yes |
|
Sectona Jump Host |
Performs hardening of the hosts, enables communication with the vault, single sign-on, and session recording. |
- |
Yes |
|
Sectona Vault Session Proxy Host
|
Provides gateway and proxy services for common protocols, web applications, and clients to communicate from client to target machine. This also enables a password at the proxy layer when web server does not have direct connectivity from web application. |
Yes |
Yes |
|
SSH Direct Proxy |
Provides gateway and proxy services for RDP access when accessed directly using native RDP clients. |
Yes |
Planned |
|
Sectona Remote Access Publisher |
It is an independent install-able component that receives requests from specified TCP Port to actual TCP Port |
- |
Yes |
|
Sectona Satellite Vault |
It is an external component built to offer alternate access to passwords in case of failure, breakdown or inaccessibility of the vault |
- |
Yes |
|
Sectona File Synchronization |
Provides sync services for object-level video log files between two servers. |
- |
Yes |
|
Sectona Vault API Extension |
Allows communication with the vault via APIs |
- |
Yes |
|
Sectona Windows Credential Provider |
Allows login to RDP Session via Sectona OTP |
- |
Yes |
|
Application Proxy |
User session distribution across servers connected to the primary database. |
Yes |
- |
|
Sectona Windows Monitoring Agent |
Sharing current activity logs of Windows Sessions as well as manage the Server Access Policy which enabled at the target server. |
Yes |
- |
Client Components
|
Component Name |
Description |
|---|---|
|
Sectona Launcher |
Independent component which communicates with the vault enables session recording and single sign-on services on the local machine. |
|
Sectona Client App |
Independent component which communicates with the vault and multi-tabbed browsing experience for RDP & SSH access. |
|
Sectona Server Privilege Control |
Enables monitoring of granular access in a privileged session initiated through Sectona Web Access. |
This illustration shows the key components in a typical deployment and inter dependencies within the system.